Experts: Ali Kazmi, EY
Facilitator: Caroline Burkart
Key Message
Organisations face myriad threats, which continuously evolve to present them with new challenges. One such evolving ‘moving target’ is cyber security – a subset of business resilience. It is being discussed by stakeholders at all levels, which suggests the industry needs a mind shift change to be able to adequately tackle the issues surrounding response, regulation and recovery.
Headlines
- Firms need to use sophisticated analytics and intelligence gathering to predict, detect and defend any impending threats or attacks to the system.
- Need to prepare to take action across the organisation’s ecosystem: execute control measure in day-to-day operations; deploy monitoring functions such as internal controls, legal department and risk management; use a strong internal audit department.
- If above two fail, need to have robust incident response capabilities to be able to manage a crisis. This includes being ready to preserve evidence in a forensically sound way and then investigate the breach to satisfy critical stakeholders – clients, regulators, investors, law enforcement and the public – who may sue for loss or noncompliance.
Key themes
Recent events e.g. digital innovation, expansion of connected products, changing regulatory landscape, and terrorist threats – point to a need for organisations to have a defensive and protective layer.
“Ecosystems are now much bigger, boundaries are fuzzy and details more complex to deal with… There is a growing need to have a whole firm response – from C-suite to each individual – because ultimately, you’re only as strong as its weakest link.”
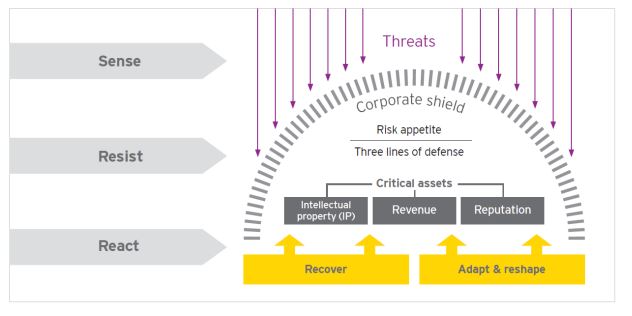
EY therefore proposes a three step approach to cyber resilience: Sense, Resist, React.
Sense: The ability of organisations to predict and deter cyber threats.
Resist: The corporate shield, starting with how much risk an organisation is prepared to take, followed by three lines of defence i.e. looking at processes and controls.
React: Extent of the organisation’s resilience i.e. being ready to deal with disruption, incident response capabilities, crisis management, preservation of evidence, and investigation of the breach.
Sense and Resist capabilities tend to be relatively well developed in organisations, and many have processes and controls in place to respond to attacks or stress situations.
React on the other hand needs further attention. For example, dozens of cyber warning alarms are likely to be going off every day but the skillset to prioritise may be missing – so how do you filter and identify, which threats are real, and which are simply noise?
Solutions include looking for patterns, gathering intelligence and collaboration. In financial services this intelligence gathering process is more advanced that in other industries.
“Some collaboration and intelligence gathering initiatives are formalised, while others are not e.g. GCHQ… Ultimately, it’s about leveraging our limited resources – have more eyes on the lookout for threats, unusual behaviours and so on – to increase our collective resilience and chances of spotting something rogue.”
Many security breaches happen over public holidays, Friday evenings and so on, when organisations do not have sufficient capacity to respond. Malware is often planted during such breaches (called ‘sleepers in the system’) that then sit dormant, on average for 3-6months, monitoring and gathering information before striking again.
So the worrying realisation is that firms can raise their corporate shields today to protect against fresh future attacks – but how do they identify what’s already sleeping in the system?
Conclusion
- Ultimately, risk cannot be avoided so we need to develop a ‘risk- radar’ and learn how to mitigate and minimise.
- Organisations are moving in the right direction – significant efforts have been made to invest in and strengthen corporate shields, and focus on Sense and Resist capabilities. Most, however are underprepared for React, with many ignoring the “it’s a matter of when, not if” adage.
- C-suite and cyber experts therefore need to be better prepared to bring their organisations back to ‘business as usual’ in the fastest time possible; learn from what happened, adapt, and reshape their organisation to improve cyber resilience going forward.